HKEY_CURRENT_USER\Software\aurora
AUI3d5OfSDist = 1|200|0|0|THNALL1L.EXE
AUI3d5OfSInst = {4FB2E350-70A2-40FB-B9C4-EC7F5B997707}
Corporation ID
http://www.abetterinternet.com/contacts.html BetterInternet, Inc. a division of Direct Revenue 107 Grand Street 3rd Floor New York, NY 10013 Phone: (646) 722-8630
Uninstall
- You have to go to the scum lord's web site - http://www.mypctuneup.com/
- You have to download and run their uninstall software
- This idiots have already proven that they can not be trusted
- They illegally installed this crap on my machine (an act of vandalism)
- The uninstall license says that something will be left on my machine when they are done
- And now they want me to trust them to remove it
Of course, I tried deleting the file, renaming the file, removing the registry entry, booting to Windows Safe mode. None of these methods work.
- The file is locked so you can not rename or delete it
- When the exe is stopped via the Windows Task Manager, it renames itself, restarts itself, and adds a new entry to the registry
- You can remove the registry entry, but when windows shuts down, it renames itself and adds a new entry to the registry
- If you start Windows in safe mode, this is the only program in the registry's run key that actually runs
This is from their web site
-
Use our FREE uninstall program to remove Aurora, BestOffers, BetterInternet, Ceres, LocalNRD, MSView, MultiMPP, MXTarget, OfferOptimizer, Twaintec, BTGrab, DLMax, Pynix, SolidPeer, Zserv and others.
To repeat, I really don't trust criminals like this to uninstall their own virus.
Uninstall 2
When booting to safe mode, this registry key is processed - nail.exe carries the payload.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon shell = Explorer.exe C:\WINDOWS\Nail.exeOn a working system
shell = Explorer.exeThe solution is to create a text file and name it nail.exe. Then copy that file to C:\WINDOWS. (If you simply delete nail.exe, it is immediately re-created.)
An alternate approach is to open nail.exe in notepad, select all, delete everything, and save the zero byte file ... overwriting the original. (Actually, I'm surprised that this works.)
Then boot into safe mode and the virus will not run.
-
The above data is based on information from
Giffmeister.
Now you can kill the rest of the virus.
- Disable svcproc.exe
- Disable DrPMon.dll
- Disable the exe in
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Reboot back to normal mode
Driver = virus 2005-07-26 DrPMon.dllThen windows won't be able to find it, and you'll have a record of the change.
If you reboot the system without disabling all 4 executables (including nail.exe), then the virus will reinstall itself, and you have to start over.
Problem Debug
I could not have solved this problem without a few hints received from the internet. However, a significant amount of data was also wrong.
Actually, it appears that there was only one single source for the technical details, and that those details were copied many places (mostly in various forums and one *.bat file). I base this statement on the fact that certain errors are present in all the instances - specifically, the instructions suggest deleting 3 files that appear to be created by Microsoft. It is possible that this is intentional misinformation to make your system more vulnerable to future attacks.
| File | Comment |
|---|---|
| C:\WINDOWS\TASKMAN.exe | I'm not sure what this is for - the Windows task manager used when Alt-Ctrl-Del is used is called taskmgr.exe |
| C:\WINDOWS\Q330994.exe | This appears to be the Microsoft IE 6 upgrade and a related uninstall file |
| C:\WINDOWS\ieuninst.exe |
The main hints that finally nailed this were that these files were involved (the comments are mine)
| Filename | Comments |
|---|---|
| C:\WINDOWS\Nail.exe | This is the program that starts the virus in Windows Safe Mode |
| C:\WINDOWS\svcproc.exe | |
| DrPMon.dll | This is a fake print port driver |
Searching the registry for Aurora found an important executable (dllvoasrs.exe) and other information.
This string is from dllvoasrs.exe (MIDL is a Microsoft C compiler)
Created by MIDL version 6.00.0361 at Tue Jul 05 13:59:07 2005
The original name of dllvoasrs.exe (the main Aurora exe file) is buddy.exe
If you search, you will find additional references to this.
Directories with traces of this virus can be found by searching your hard drive for
THNAL*
aur* this found the main Aurora install file (verified by looking inside it)
C:\Documents and Settings\username\Local Settings\Temp\XQG\aurareco.exe
One reference said
-
Create a text file called nail.exe and place it in the c:\windows directory. Over write the existing file and set it's attributes to read-only.
In fact, that became a major part of the debug technique
- Copy a questionable exe file to another directory
- Edit the file with Notepad
- Delete ALL the data
- Save the empty file without changing the extension
- Change the file properties to readonly so that the virus could not replace the file (very important)
Related Programs
dsr.dll
Does not specify who designed (owns) this program.
HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer
Browser Helper Objects = {00F1D395-4744-40f0-A611-980F61AE2C59}
DSrch.PopupBrowser PopupBrowser Class {8B51FC2F-C687-40a3-B54A-BB9EBF8D407F}
DSrch.LeftFrame LeftFrame Class {CE27D4DF-714B-4427-95EB-923FE53ADF8E}
DSrch.BottomFrame BottomFrame Class {E2D2FE40-5674-4b77-802B-EC86B6C2C41D}
DSrch.PopupWindow PopupWindow Class {E311D3A5-4A3B-4e49-9E0A-B40FAE1F0B28}
dsr.exe
CompanyName Mimar Sinan International FileDescription Emissary InternalName autonomy LegalCopyright Copyright © 1992-2000 Mimar Sinan International. All rights reserved. OriginalFilename autonomy.exe ProductName MimarSinan Emissary, MimarSinan Charm FamilyThis program is suspicious because
- A large part of the file appears to be encrypted
- Company focuses on installation, setup authoring tools (from the Google search results)
- Mimar Sinan is the name of a university in Istanbul, Turkey
- Mimar Sinan is the name of a mosque in Turkey
ImIServer IEPlugin Object Recognized Category : Data Miner ProductName : MimarSinan Emissary, MimarSinan Charm Family OriginalFilename : autonomy.exehttp://computing.net/security/wwwboard/forum/15971.html
- Associates autonomy.exe with tdtb.exe, one of the files associated with Aurora
- Found * explorer.exe c:\windows\nail.exe *
- Listed DrPMon.dll as malware
- HKLM\system\controlset001\control\print\monitors\zepmon - listed as malware
dinst.exe
svcproc.exe
svcproc.exe is a hijacker which means it will intermittently change your Internet Explorer settings / Desktop to the link of itís authorís sponsors.
Multimpp
-
HKEY_CURRENT_USER\Software\Multimpp
These are also related
C:\WINDOWS\preInMPP.exe referenced in C:\Documents and Settings\username\Local Settings\Temp\multimpp.inf C:\WINDOWS\preInsln.exe looks very similar
Cookies
Research (using FileMon) indicates that this data is encrypted and written to several cookies (even if cookies are turned off - this is possible because IE is not writing the cookie, the virus is).
It appears that these cookies (yes, it is plural) include information on which virus and spam protection programs are loaded on your machine.
If you then click one of their adds, then the cookie, with stolen information, is sent to the site.
Notes
C:\Documents and Settings\username\Local Settings\Temp\XQG\aurareco.exe
The virus pops up several dialog boxes that look like they come from Microsoft. (In fact, Microsoft should sue them for it. It is very convincing.) Only the hidden icon gives it away - use alt-tab to see the virus icon (a circle with arcs on it).
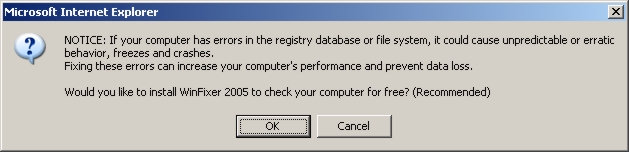
Since WinFixer is provided by a known virus writer, it should be avoided at all costs. (Clicking either button or the x in the upper corner starts the download.)

This LOOKS like a cookie download warning - it is not. If you click ANY button, this parasite will try to download some program.
I apologize for repeating these warnings here (in a reduced font size) ... but the search engines
don't index information inside html comment tags.
NOTICE: If your computer has errors in the registry database or file system,
it could cause unpredictable or erratic behavior, freezes and crashes.
Fixing these errors can increase your computer's performance and prevent data loss.
Would you like to install WinFixer 2005 to check your computer for free? (Recommended)
...
The Web site "www.tripreservations.com" has requested to save a
file on your computer called a "cookie." This file may be used to
track usage information. Do you want to allow this?
- I really don't want to provide live links to the scum lords that created this virus. (I would feel bad if I helped you get infected.)
-
webhelper4u
provides several interesting articles
- the Aurora Transponder provides technical details for a slightly different version than the one I fought - different exe files
- The Transponder Gang - Main index to a whole family of related parasites, including over 300 related files, including the Aurora variant
- Spyware Lawsuit Alleges Computer Hijacking April 5, 2005 - well, this is a start, but cyber-terrorism would be more appropriate.
- Aurora install source revealed explains how Aurora is installed via BitTorrent - however, on my system, "btdownloadgui.exe" was not found. additional reading
-
Spyware Floods In Through BitTorrent
is a must read - it provides an interview with the scum lord himself
-
Daniel Doman, the chief technology officer at Direct Revenue, said that the daily uninstall count was "in the thousands."
... "The notion that the user has accidentally found all this software on his machine is false."
- Remove Aurora Virus (nail.exe) provides Aurora_removal.zip and instructions to remove this parasite. I provide this reference with a warning NOT to use their uninstall program. My analysis indicates that, while it does appear to remove most of the Aurora virus, it also removes 3 Microsoft executables without explaining why. On the other hand, deleting TASKMAN.EXE has no real effect since it is immediately recreated ... unless you follow the instructions and disable System Restore. It also DOES NOT remove the exe started via the run key (because the filename changes so often). (Be careful)
- Aurora Networks is not in any way connected with this virus. But, because of a high number of emails, they HAVE written a great, must read, page discussing the problem and providing many good links.
-
Lavasoft (Ad-Aware) claims to be the first antispyware vendor to remove the nail menace
-
Lavasoft is the first antispyware vendor to successfully react on the problem by releasing an effective tool to clean Nail.exe and DrPmon.dll from your computer. The tool is an updated version of the Lavasoft VX2 Cleaner, a plug-in to Ad-Aware SE and downloadable at our site free of charge.
I am not sure when the Lavasoft solution was available, but
- There is a date of 12 August 2005 on their page (they also have a news article with the same date and info)
- There is no mention of the Aurora virus
- This page (my page) was first written 7-26-05, available via Google 8-08-05
Author: Robert Clemenzi