ErrorSafe (www.errorsafe.com, 66.244.254.63) (from McAfee)
-
Notice that both Winfixer and errorsafe have the same IP address.
Comparison of the Winfixer.com and errorsafe.com pages indicates better than 90% identical.
In my opinion, these are both written by and hosted by the same person.
This was found via Google
Which indicates that the site is actually in the North Eastern USA.
http://www.softwareprofit.com - this link is in the Winfixer.com web page
This is what WinFixer wants to install
imagesrvr.com appears to be a simple reseller - so they are probably not directly involved
with this parasite.
This has the same snailmail address as winfixer.com.
This is another WinSoftware Ltd. site
KTVU (Channel 2 in Oakland, CA) produced this
Fraudware Special Report
(YouTube) on the lawsuit.
They repeatedly refer to WinFixer as a virus.
Not knowing any better, Beatrice Ochoa
got tied of the continuous popups and purchased a copy of WinFixer ...
which eventually rendered her computer's hard drive unusable.
This virus eventually cost Beatrice over $1,000.
In 2007, the lawsuit was dropped because Mr. Bochner
lacked the resources and expertise.
Personally,
I think that a class action suit was the wrong approach.
Federal crimes have been committed and
the FBI should be pursueing these criminals ...
not a private lawyer.
Unfortunately, the FBI told Mr. Bochner that they were not interested in protecting
the American people.
Mr. Bochner also claims to have uncovered a probable link between Symantec and WinFixer.
Apparently, the same people who wrote WinFixer also wrote a bogus Symantec anti-virus program.
It would popup on people's machines and indicate that the Symantec license had expired.
Of course, clicking on renew sent you to a bogus site ... and they simple stole
lots of money.
In 2004, Symantec sued them, and eventually reached a confidential settlement.
(WinFixer was discovered in 2005 and Symantec was not able to detect or remove it
until .... well at least until 2006. As of Sept 2008, I still don't think that
their programs can detect the versions I saw in 2005.)
Unfortunately, this means that the connection/truth will never be known.
In fairness to the defendants, it was never proven that they are the people behind
WinFixer. But, whoever the people are who distributed the virus should be
brought to justice.
Additional references
This is the dialog box that the Aurora virus displayed suggesting that WinFixer is just super.
Since WinFixer is provided by a known virus writer, it should be avoided at all costs.
(Clicking either button or the x in the upper corner starts the download.)
I apologize for repeating this warning here (in a reduced font size) ... but the search engines
don't index information inside html comment tags.
WinFixer 2005 free download. WinFixer 2005 is a useful utility to ...
http://www.freedownloadscenter.com/Utilities/System_Maintenance_and_Repair_Utilities/WinFixer_2005.html
Any site that calls WinFixer "a useful utility" should be avoided.
Domain Name: FREEDOWNLOADSCENTER.COM [66.246.72.50]
Registrant:
Victor Sazhin
Minskaya st, house 3
Moscow, Moscow 121108
RU
(095)724-3536
Reverse DNS provides
220918.ds.nac.net [66.246.72.50]
It sells both WinFixer 2005 / WinAntiSpyware 2005 and WinAntiVirus PRO 2006
locator1.cdn.imagesrvr.com/sites/winfixer.com/www/download/2006/WinFixer2006FreeInstall.cab
Domain name: ERRORSAFE.COM [66.244.254.64]
Registrant:
ErrorSafe, Inc.
Rua Luiz de Conto, 133
Toledo, Parana CEP 85914-045
BR
Administrative Contact:
Parizotto, Jardim info@errorsafe.com
Rua Luiz de Conto, 133
Toledo, Parana CEP 85914-045
BR
+1.7865130244 Fax: +1.7865130244
Notice that the IP address is different than what McAfee indicated,
but not by much.
Reverse DNS provides
rr-grp1.yyz1.cl1.setupahost.net [66.244.254.64]
Domain name: SOFTWAREPROFIT.COM [66.244.254.43]
Registrant:
SoftwareProfit
P.O. Box 3
Kiev, NA
UA
Administrative Contact:
Hostmaster, SoftwareProfit hostmaster@softwareprofit.com
P.O. Box 3
Kiev, NA
UA
+(380) 97 939 09 44 Fax: +(380) 97 939 09 44
Reverse DNS provides
box43.yyz1.setupahost.net [66.244.254.43]
Domain name: WINANTISPAM.COM [66.244.254.46]
Registrant:
Innovative Marketing, Inc.
1876 Hutson Street
Belize City, NA
BZ
Administrative Contact:
Hostmaster, Innovative hostmaster@innovativemarketing.com
1876 Hutson Street
Belize City, NA
BZ
555-123-1234 Fax: 555-123-1234
Come ON - 555-123-1234 - definitely a fake
WinSoftware Ltd. sites
billingnow.com [66.244.254.63]
innovativemarketing.com [66.244.254.177] Fax: (123) 456-7890
softwareprofit.com [66.244.254.43]
winadblocker.com [66.244.254.46]
winantispam.com [66.244.254.46]
winantispy.com [66.244.254.46]
winantivirus.com [66.244.254.63]
winantiviruspro.com [66.244.254.63]
wincontentfilter.com [66.244.254.46]
windrivecleaner.com [66.244.254.46]
winfirewall.com [66.244.254.46]
winfixer.com [66.244.254.64] 127.0.0.1 as of 04-15-07
winnanny.com [66.244.254.46]
winpopupguard.com [66.244.254.46]
winprivacyguard.com [66.244.254.46]
winpluspak.com [66.244.254.63]
errorsafe.com [66.244.254.64]
systemdoctor.com [66.244.254.63, 66.244.254.64]
New IP Addresses - 11-08-07
softwareprofit.com [66.244.254.180]
winfixer.com [ ] no longer found
errorsafe.com [85.17.4.103]
systemdoctor.com [85.17.4.103]
The last 2 are located in the Netherlands.
http://www.dnsstuff.com/tools/whois.ch?ip=85.17.4.103
LeaseWeb
P.O. Box 93054
1090BB AMSTERDAM
Netherlands
www.leaseweb.com
LeaseWeb is owned by
www.ocom.com [85.17.8.34]
which appears to be legitimate.
C:\>tracert 85.17.4.103
Tracing route to 85.17.4.103 over a maximum of 30 hops
The first 7 are not important
8 28 ms 210 ms 211 ms TenGigabitEthernet8-4.ar3.DCA3.gblx.net [64.210.21.57]
9 100 ms 100 ms 101 ms 64.213.76.150
10 103 ms 105 ms 105 ms 62.212.95.142
11 100 ms 101 ms 100 ms 85.17.4.103
Trace complete.
If you simply try to see the page at
http://85.17.4.103/asd
you will see that the site is owned by viragehosting.com
(from the webmaster email address).
Lawsuit
Additional claims include
Lawyer Joseph M. Bochner's personal blog
Notes
WinFixer is closely related to Aurora Network's Nail.exe hijacker/spyware program. In worst case scenarios, it may embed itself in Internet Explorer and may be nearly impossible to remove. The program is also closely related to the Vundo and Virtumonde viruses.
When I checked the McAfee site for info on Vundo, I found the instructions to manually remove the program.
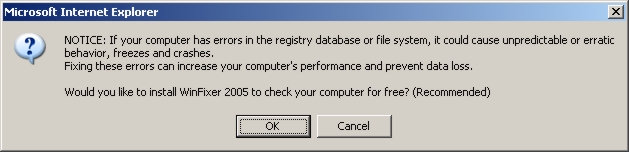
NOTICE: If your computer has errors in the registry database or file system,
it could cause unpredictable or erratic behavior, freezes and crashes.
Fixing these errors can increase your computer's performance and prevent data loss.
Would you like to install WinFixer 2005 to check your computer for free? (Recommended)
Unfortunately, wikipedia has a serious problem with information rot and
most of the useful information is disappearing.
URL: http:// mc-computing.com /
Parasites /
WinFixer_parasite.html